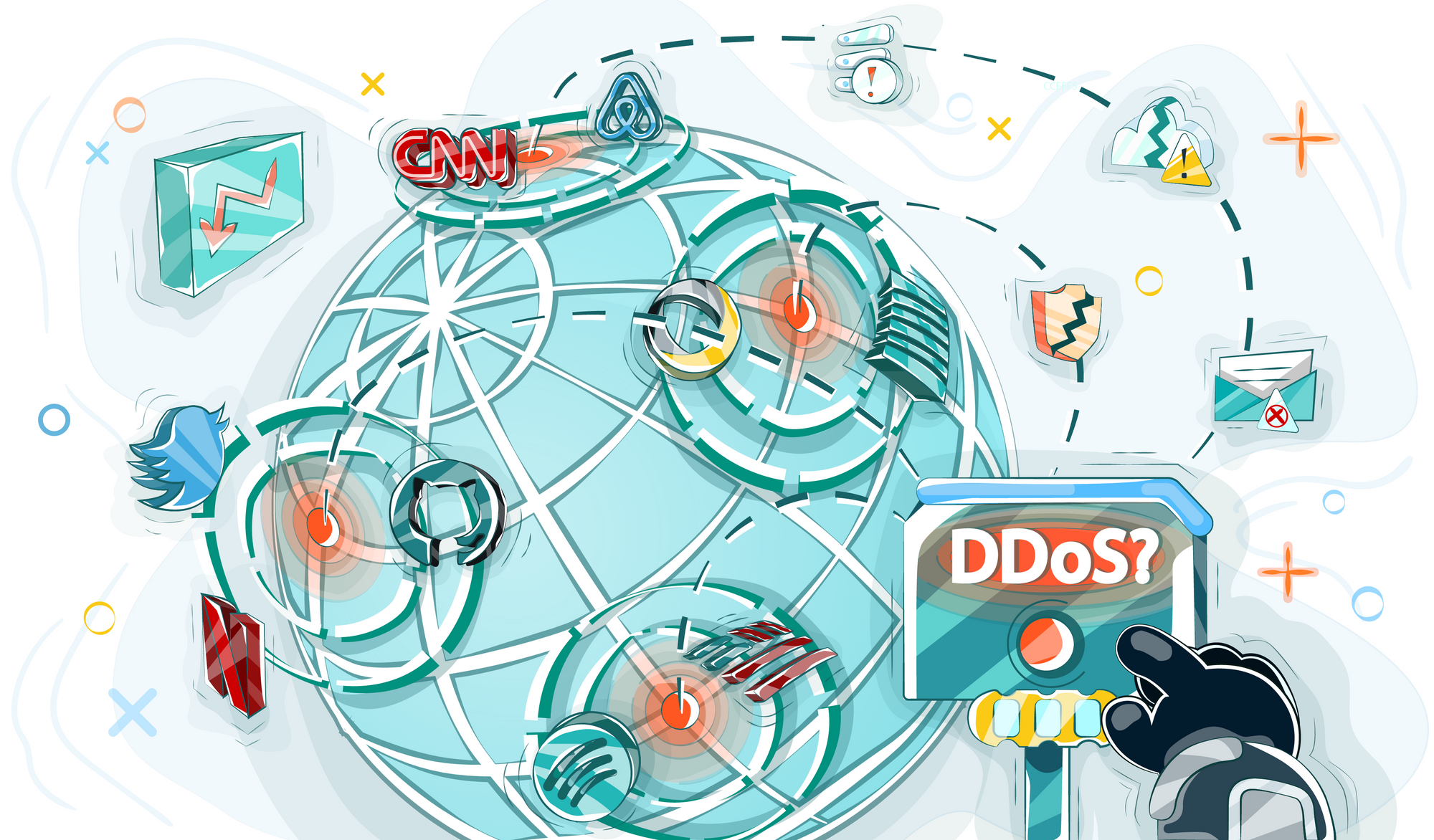
From 50 to 440 thousand dollars – approximately such amounts are lost by medium and large enterprises as a result of a single DDoS attack. Companies suffer considerable losses due to the downtime of their resources, and they need to spend another part of their funds on restoration. But things for the world’s giants are even worse: a cyber-attack on a corporation of the Amazon level can lead to billions of losses. We have already talked about the essence of DDoS attacks and what their varieties are. In this article, we will give examples of the most demonstrative cases which went down in history and directly affected the welfare of the world giants.
Resistance Project
On February 7, 2000, the Yahoo! service, the leading search engine of the time, was brought down. The site was inaccessible to users for an hour. Following that event, the resources of eBay, CNN and Amazon almost failed to work for a whole week. All these problems were caused by one of the first major DDoS attacks, which was organized by a hacker with the nickname Mafiaboy.
A 16-year-old Canadian Michael Kals turned out to be the culprit in these failures. The teenager launched the “Rivolta” project, which means “Resistance” in Italian. According to the hacker, the goal was to establish the dominance of his group called TNT in the cyber world.
Rivolta was an attack of the denial of service category. Mafiaboy took advantage of the Y2K vulnerability. Alongside, as part of his project, the young man hacked into 50 different networks, installed the Sinkhole software on them and tried to flood the sites that were selected as targets for the attack.
The Y2K vulnerability is also known as “the Year 2000 problem”. Its essence is as follows: in many software products developed in the 20th century, the year is displayed in two digits. Thus, the developers did not provide correct displaying of the date when switching to the calendar for the 21st century. For example, the 01.01.00 programs were identified as those of the beginning of year 1900, not 2000. Such shortcomings led to critical failures in various automated systems.
The Canadian police managed to find the teenager quickly through the forums where he boasted of his exploits. Initially, Michael Kals’s lawyers denied the liability of the defendant. The defense insisted that the child conducted only uncontrolled tests. However, during the trial, the hacker pleaded guilty to most of the charges. He received a sentence of 8 months of open detention, one year of probation, limited use of the Internet and a small fine.
The attack resulted in tremendous damages not only to the companies whose sites were targeted by Michael Kals. Significant losses became tangible for the whole economy. Matthew Kovar, a senior analyst at Yankee Group Research Inc, claimed to reporters that these attacks had caused $1.2 billion of global economic damage.
Operation Ababil
In 2012, large-scaled DDoS attacks were launched in the United States, which disabled several American financial organizations and banks for some time. Operation Ababil is a series of cyber-attacks carried out by a group of cyber fighters called Izz al-Din al-Qassam. Hackers began to act in order to avenge for the anti-Islamic film, which was uploaded to the Internet and insulted Mohammed, the Prophet of Islam.
DDoS attacks were carried out in three phases. Every time, the cyber fighters announced a list of organizations that they were going to attack. The main requirement of the group was to remove the above mentioned film. To achieve the fulfillment of this demand, the hackers conducted cyber-attacks aimed at various banking and financial organizations:
- Bank of America September;
- New York Stock Exchange;
- Chase Bank;
- Wells Fargo;
- U.S. Bank;
- PNC Bank.
Other American banks were also targeted by the Islamic hackers. In total, attacks were aimed at 12 financial institutions.
Assessing the power of the Ababil operation, experts and American politicians, also expressed an opinion that the attacks were carried out not by a group of activists, but by the Iranian government as a response to the economic sanctions of the West.
DDoS attacks within the Ababil operation were quite large-scaled. The peak values were up to 70 gigabits per second, which is considered a heavy load by 2012 standards. The hackers managed to temporarily disable some US banks and disrupt their customers’ access.
Cyber Attack on Dyn
On October 21, 2016, users could not access more than 80 sites for several hours. Among the affected resources were popular platforms Twitter, Spotify, Airbnb, Netflix, CNN, BBC, The New York Times and many other resources.
The problems occurred due to numerous denial of service attacks against the DNS provider Dyn. The estimated load was approximately 1.2 terabits per second. At that time, such an indicator was the ground to consider it the largest cyber-attack in history.
The cyber-attack on DynDNS is remarkable for being carried out with the use of the malware called Mirai. This is a botnet that connects to IoT devices with vulnerabilities, “infects” them and launches a botnet. Mirai mainly connects to devices whose owners have saved the default passwords set by the manufacturers. During the DDoS attack on DynDNS, more than 100 thousand devices were infected, among them IP cameras, routers, printers, baby monitors.
For the first time, Mirai DDoS attacks were carried out about a month before the Dyn cyber-attack. The target of hackers was the site of Brian Krebs – an information security specialist and journalist. Shortly before that, he published an article on cyber groups that use botnets to carry out DDoS attacks. The intervention lasted from September 21 to September 25, 2016. According to cyber security experts, the Mirai botnet has infected more than 560 thousand cameras from the Internet of things category.
In total, three attacks had to be fought back during that day. The chronology (indicating hours according to North American Eastern time) was as follows:
- From 7.00 a.m. to 9.20 a.m. continued the first attack, which was successfully repulsed;
- At 11.52 a.m. the intervention was repeated, after which the resource users began to leave complaints about the lack of access;
- From 4.00 p.m. to 6.11 p.m. the third attack was taking place.
Thus, Dyn was able to solve the problem within less than 12 hours.
In the majority of cases, these were residents of the US east coast who faced access problems. For ordinary users, the situation led to the fact that it was impossible to use the usual services: play on the Sony PlayStation, watch movies and TV shows on Netflix or listen to music via Spotify. The situation was more problematic for people who made money transfers, for example, via PayPal, Visa or tried to book accommodation on Airbnb. Amazon’s West European affiliate suffered a separate DDoS attack. Total financial losses amounted to approximately $110 million. The DNS provider itself also suffered significant damage: approximately 8% of the company’s customers stopped working with Dyn.
The Largest Attack on GitHub
On February 28, 2018, GitHub became the target of one of the largest DDoS attacks in history. Incoming traffic peaked at about 1.35 terabits per second, which at that time was a record. The cyber-attack took the service offline for less than 10 minutes.
Vulnerable Memcached servers were blamed for what happened. This is software that allows to cache data in RAM based on the distributed hash table paradigm, which improves application performance and removes the load from database servers. Just a week before the intervention, cyber security experts reported that hackers began using Memcached to amplify DDoS attacks.
5 days after the cyber-attack on GitHub, hackers broke the record again. This time one of American providers became a target. The maximum load was 1.7 terabits per second.
This cyber-attack did not bring significant damage to GitHub, as user data was not affected. Apart from to the fact that the service stopped working for about 10 minutes, there were no consequences.
Testing a New Botnet: Attack on Wikipedia, Twitch and WoW
On September 6-8, 2019, an unknown Twitter user with the nickname UKDrillas practically brought down the Wikipedia site almost live. Simultaneously, DDoS attacks on Twitch and the servers of the World of Warcraft Classic game were launched.
Presumably, the hacker or an entire group was testing a new malicious botnet. As a result of the cyber-attack, Wikipedia was inaccessible to residents of the United States and Europe for 3 days. To resume the resource, Cloudflare, a company providing services to mitigate DDoS attacks, was referred to for help.
Blizzard Entertainment, the developers of World of Warcraft Classic, were troubleshooting for 2 days. The company’s security team worked with local and international law enforcement agencies to track down the attacker. As a result, the hacker was found and arrested, although the identity of the cybercriminal was never disclosed.
AWS DDoS Attack
On October 22, 2019, Amazon suffered from a cyber-attack once again. This time, it was its subsidiary, Amazon Web Services, that was targeted. The cloud service went down for 8 hours. The attack was aimed mainly at the Router 53 DNS service.
By the way, every year cloud services are increasingly becoming targets for DDoS attacks. In 2016, only a quarter of cyber-attacks accounted for “clouds”, while as early as 2018, approximately 47% of such sites were affected by an interference.
Malfunctions began at 10.30 a.m. local time. The company was sending out messages to its customers during this process, which made it clear that its DNS servers were indeed subjected to a DDoS attack. At 6.30 p.m., representatives of the Amazon announced that all the problems had been resolved.
The consequences of the failures were successfully minimized. However, such vulnerability casts doubt on the effectiveness of the AWS Shield, a platform specifically designed to safeguard against DDoS attacks. The significance of this incident is also discussed in the leading analytical companies. Thus, Neustar First Vice President Anthony Chadd said that this attack should serve as a reminder to security leaders that they need to constantly provide cyber protection at several levels: “Prevention is always better than treatment. The price of inaction – from reputation damage to additional investments in technology, compensation, and possibly regulatory action – may have an undesirable impact on the final result”.
At the present moment, it’s quite easy to launch a cyber-attack on a website of competitors. The price per hour of a DDoS attack is $10-20. It is a trifle for the customers of such services, but the targets will feel the consequences. Of course, companies that are far from the level of Amazon, eBay or other giants of the world market will not suffer millions of losses from DDoS attacks. However, the damage is likely to be substantial. It’s not just about a few-hour downtime, which can be disastrous for an online store. The list of losses may include confidential information or reputational damage to the brand.
To ensure full security of the resource, we highly recommend paying attention to multilevel protection. This is one of the most effective ways to prevent DDoS attacks. Our protection allows you to withstand a DDoS attack with a load of up to 100Gbps. We do not use extraneous services for filtering, so cleaning occurs without delay. Additional benefits of King Servers protection include:
- Geographically distributed filtering with a network capacity of 1Tbit / sec;
- Hardware firewall;
- Round-the-clock availability of resources.
It takes only 10 minutes to connect and configure protection. We provide full safety at a minimum cost for you! Be protected on our servers.